1 Which protocol in its default configuration downloads e-mail messages to the client computer and deletes them from the server? ...

Talk Less Do More

1 Which protocol in its default configuration downloads e-mail messages to the client computer and deletes them from the server? ...

1 Refer to the exhibit. A PC requests an IP address from the server. Which two protocols are used at the TCP/IP application la...

1 What is a major characteristic of asymmetric Internet service? Download speeds and upload speeds are equal. Download speeds are faste...
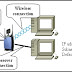
1 What should a network administrator do first after receiving a call from a user who cannot access the company web server? Reboot the w...
1 Identify three techniques used in social engineering. (Choose three.) fishing vishing phishing spamming pretexting junk mailing ...

1 Why is IEEE 802.11 wireless technology able to transmit further distances than Bluetooth technology? transmits at much lower frequenci...

1 How large are IPv4 addresses? 8 bits 16 bits 32 bits 64 bits 128 bits 2 Refer to the graphic. A user at the workstatio...

1 Which definition describes the term Internet? a group of PCs connected together on a LAN a group of PCs connected together by an ISP ...

1 Which term is used to describe the process of placing one message format into another format so that the message can be delivered acros...

1 Which method of interacting with an operating system involves typing commands at a command prompt? CLI GUI redirector kernel transl...